Research shows around 40% of connected assets remain unmonitored meaning organizations are vulnerable to unseen risks.
Without a clear, real-time view of all assets—managed and unmanaged—understanding your attack surface and proactively addressing vulnerabilities and other security findings becomes near impossible.
Knowing which assets you have and identifying those that pose the greatest risk is the first step to preventing exposures from escalating into serious threats.

Protect your entire attack surface and manage cyber risk exposure in real time
With comprehensive visibility over your assets, you can adopt a proactive cybersecurity posture to keep them secure, reduce alert fatigue, and streamline workflows to address threats faster and more efficiently
Know what you have
Lack of visibility leaves your organization vulnerable. Understanding every asset, its usage, associated security findings, and who is interacting with it is critical to reducing risk. This comprehensive insight enables you to see the full scope of your digital environment and identify hidden cyber risks.
Take proactive measures
Cybersecurity teams face huge backlogs of security findings and alerts awaiting review. To regain control, organizations must focus on the most critical findings by combining severity and exploitability with asset risk and business criticality.
Streamline workflows and systems
Reactive security results in delayed responses to breaches. Establishing clear workflows and automated systems ensures faster detection and remediation, drastically improving your ability to manage security and reduce mean-time-to-resolution.
Discover, contextualize, enrich and profile every asset
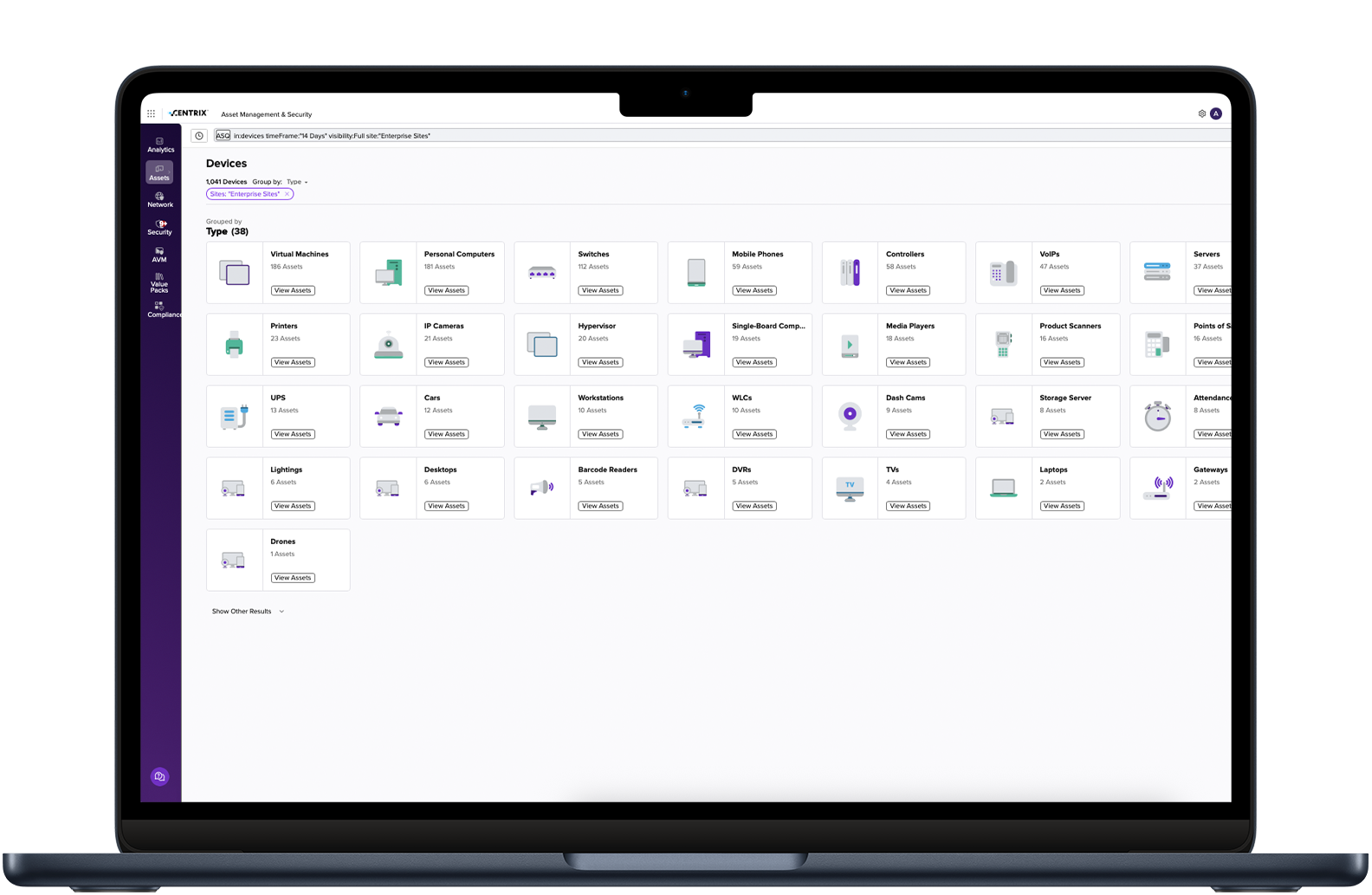
Complete asset discovery
By gaining instant visibility into all your connected assets—whether managed, unmanaged, or shadow IT—you can uncover hidden vulnerabilities, reduce blind spots, and take proactive action to protect your organization before threats emerge.
Real-time contextualization
See not just what assets you have, but also who is using them and how they behave, giving you the opportunity to assess risk and prioritize response with confidence.
Proactive risk reduction across IT, IoT, OT, IoMT
Break down silos and gain a unified, real-time view of all your assets, no matter their type or location. With complete visibility, you can focus on what matters most—proactively reducing risk by prioritizing your most critical assets and using early warning intelligence to stay ahead of threats.
Take proactive measures, detect threats, stop attacks
Prioritized threat detection
Identify and focus on the findings and alerts that pose the greatest risk to your business. Armis Centrix™ reduces time spent on manual assessment and prioritization by 80%, letting your team work smarter, not harder.
Proactive threat prevention
Create automated workflows to help you take immediate, prioritized action on threats. Using our platform to do precisely this, organizations improve mean-time-to-resolution by up to 75%.
Comprehensive protection at scale
Whether your assets are IT, OT, IoT, medical, physical or virtual, from the ground to the cloud, we offer protection for every type of connected asset, including those that other tools can’t see
Establish workflows and track risk reduction
Intelligent risk tracking and resolution
Monitor and track the progress of risk mitigation efforts across your environment with AI-driven insights. With dedicated cyber exposure management dashboards and dashlets, you can quickly identify and address bottlenecks, ensuring that risk reduction is both efficient and effective.
Smarter asset intelligence
Leverage the largest AI-driven Asset Intelligence Engine to establish known-good behaviour baselines and continuously monitor for deviations, ensuring accurate prioritization and remediation.
Streamlined compliance and oversight
Simplify compliance efforts with granular Role-Based Access Control (RBAC), pre-built integrations, and continuous monitoring. Armis Centrix™ ensures every action aligns with security frameworks and regulatory standards.
Armis Centrix™
Armis Centrix™, the cyber exposure management platform, is powered by the Armis AI-driven Asset Intelligence Engine, which sees, protects and manages billions of assets around the world in real time.
Our seamless, frictionless, award-winning platform proactively mitigates all cyber asset risks, remediates vulnerabilities, blocks threats and protects your entire attack surface.
Armis Centrix™, the cyber exposure management platform, protects your entire attack surface and manages cyber risk exposure in real time. The platform boosts operational resilience and supports cross-functional alignment in even the most complex organizations to ensure mission critical systems remain fully protected. Armis Centrix™ is the foundation on which modern cyber programs build and optimize.

Discover Armis Centrix™
Asset Management and Security:
From Chaos to Control
Benefit from a powerful and streamlined approach to asset management that enables your agency to discover and classify every managed and unmanaged asset in your environment. Quickly uncover and eliminate gaps and optimize your organization‘s security, define policies to enforce security controls on your devices, and ensure compliance with regulations and the protection of national interests. Gain unique, actionable cyber intelligence to detect and address real-time threats across the entire asset attack surface.
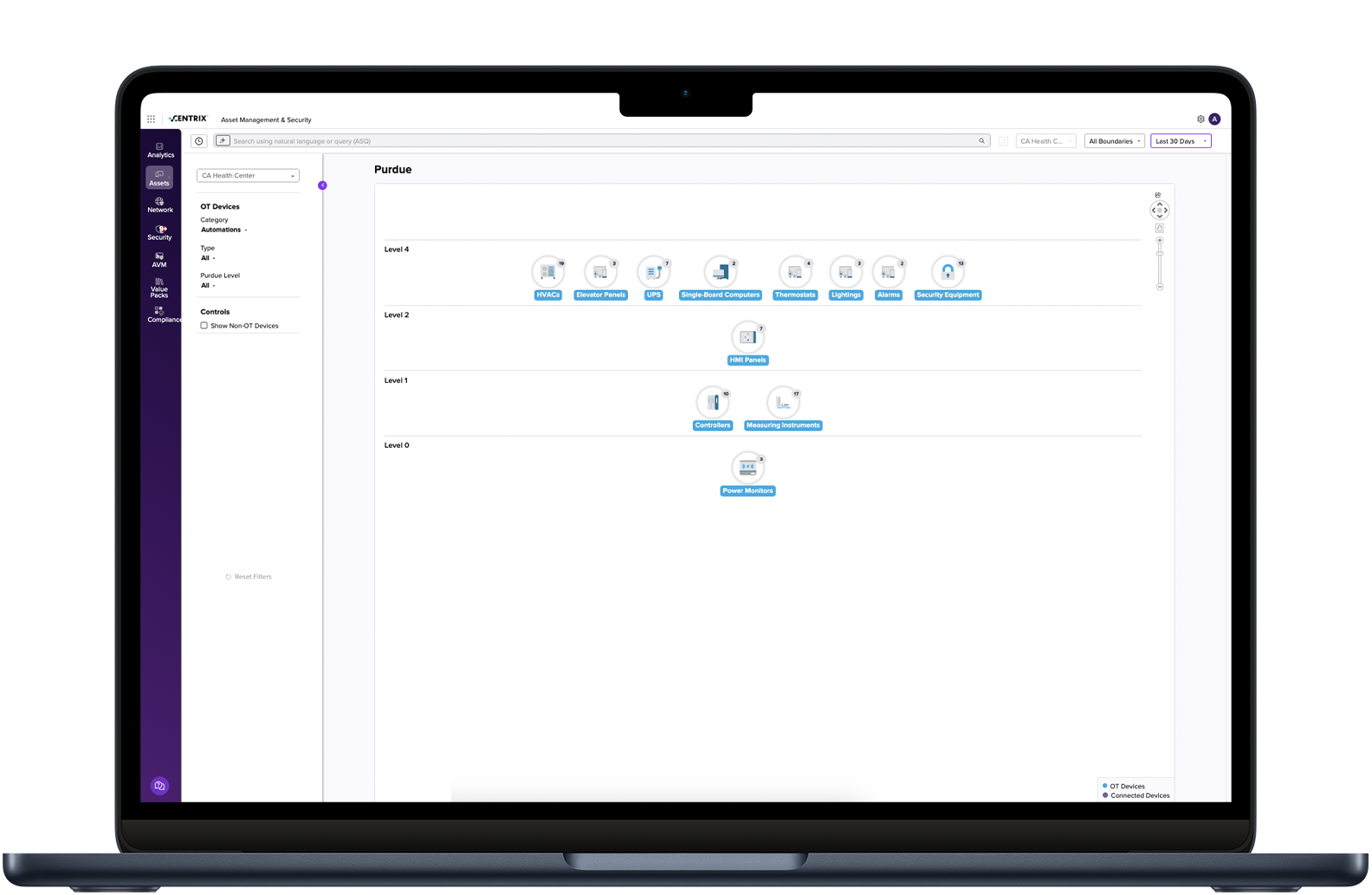
OT/ IoT Security: Keep Critical Infrastructure Safe and Secure 24/7
Understand Operational Technology (OT) risks. See, protect and manage every operational technology device — including SCADA, PLCs, and DCS – and the support assets that keep national security interests and critical assets safe and operational. The scope of Armis Centrix™ extends to your entire environment – from the front line to the executive branch. Enjoy the freedom to choose with flexible deployment options of on-premises, SaaS or hybrid delivery.
Medical Device Security: Continuous Security, Optimized Utilization
Armis Centrix™ identifies and secures the IT, OT, IoT, and IoMT assets essential to connected care delivery. Optimize your security posture and manage the complex medical devices that ensure healthcare delivery is protected. Take the next step in securing both managed and unmanaged devices without disruption and protect your assets and the people relying on them.
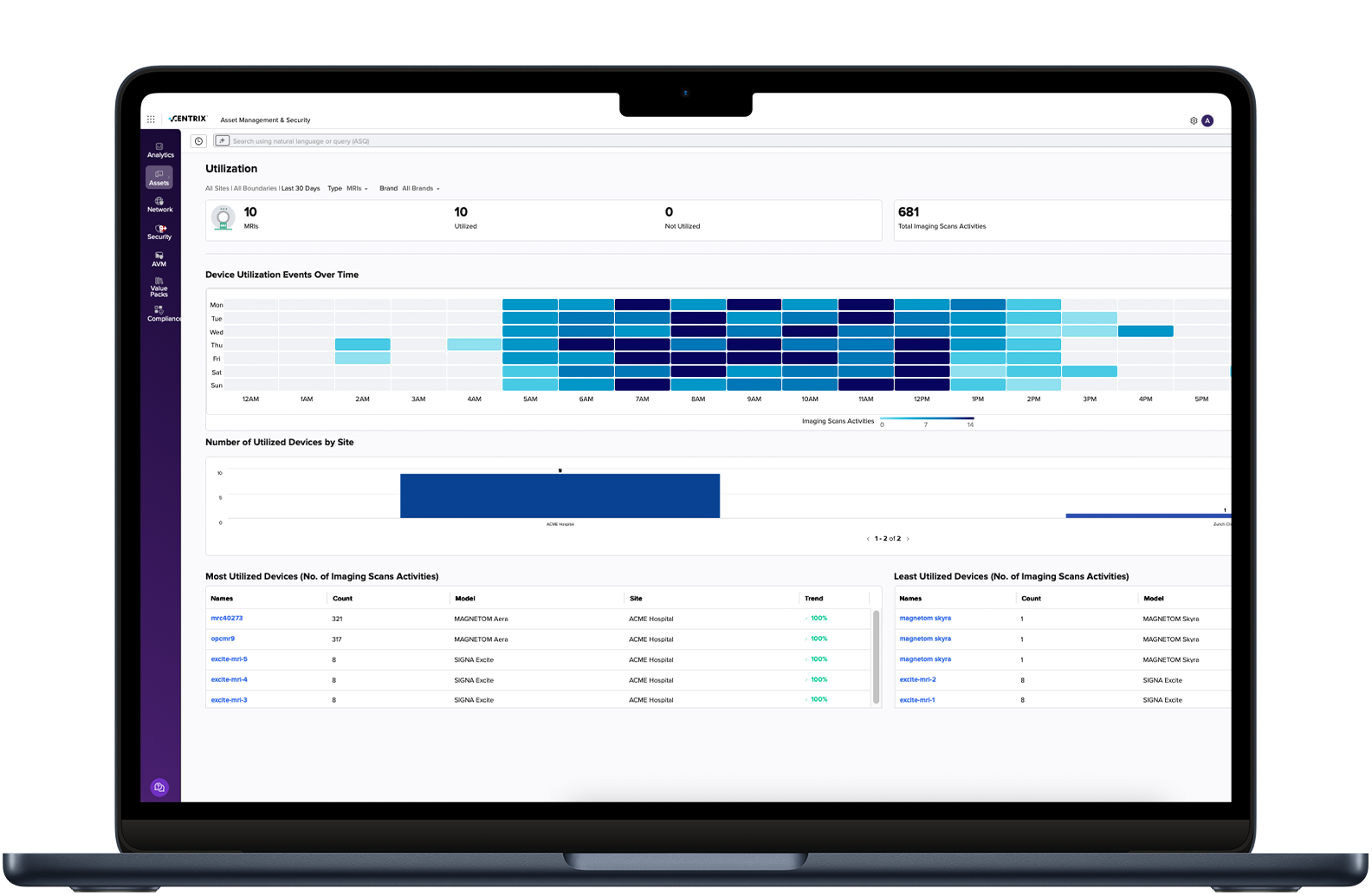
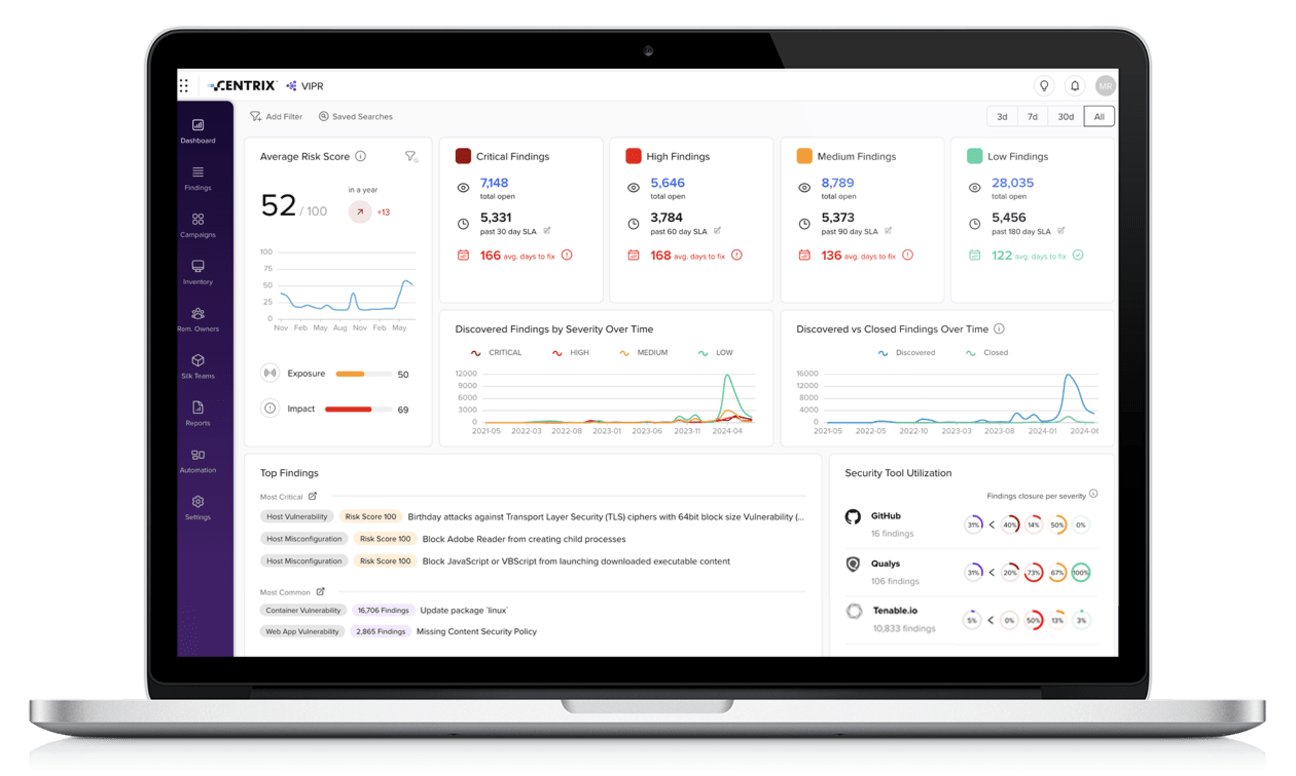
VIPR Pro - Prioritization and Remediation: Connect the Findings to the Fix
Identification, deduplication, contextualization, prioritization assigning and mitigation helps Security and IT Operations teams focus their efforts on the most pressing vulnerabilities and risks. When your teams know exactly which critical assets are affected by precisely which vulnerabilities, they can act quickly to remediate the issues that pose the biggest threat to the mission.
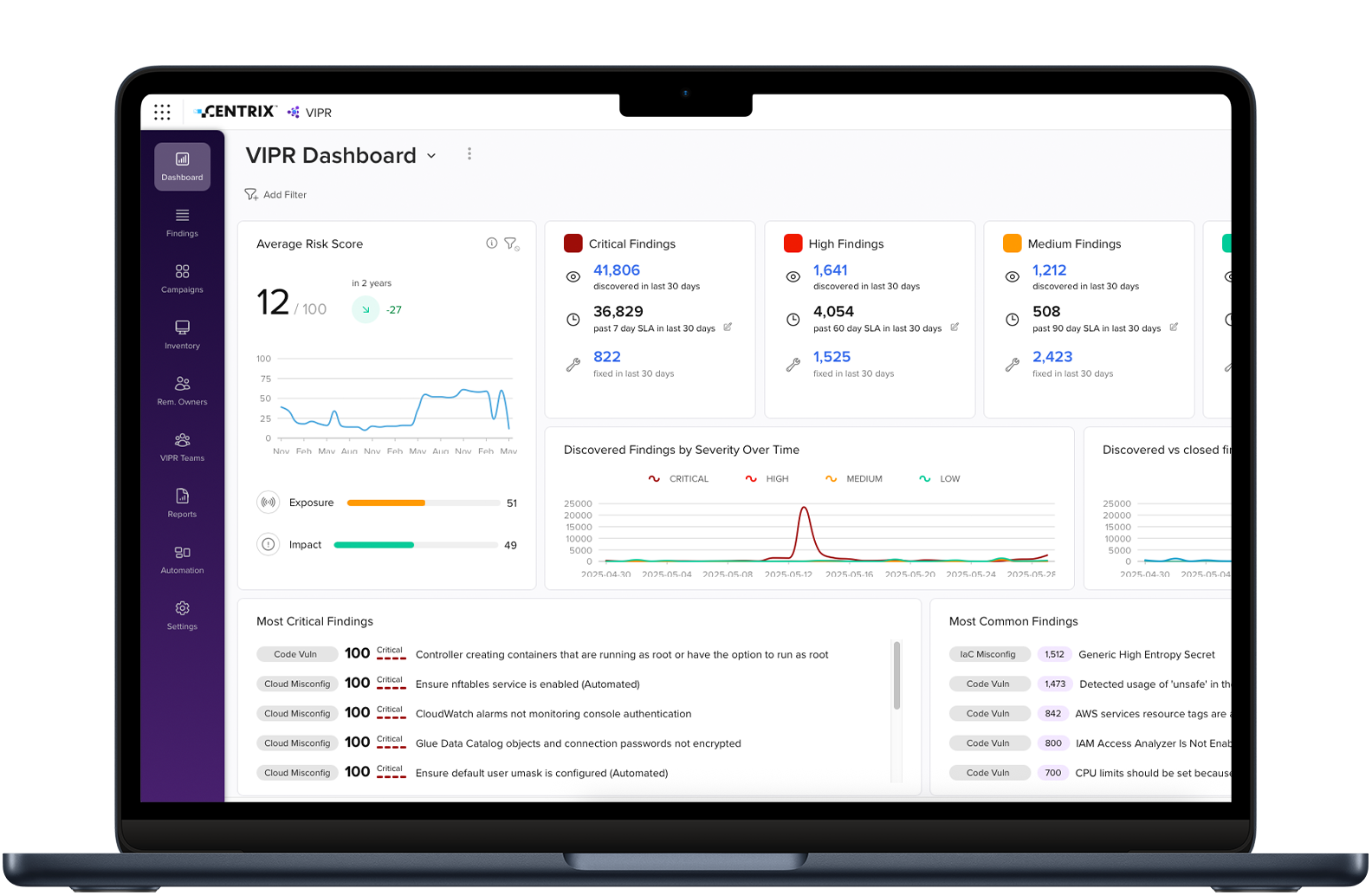
Early Warning: Anticipate & Stop Attacks Before They Start
Transform the way you do security and flip the script on hackers by identifying and stopping attacks before they are even launched. Armis Centrix™ for Early Warning uses cutting-edge AI technology that leverages intelligence on what threat actors are exploiting in the wild or are about to weaponize. Shift your focus from reactive chasing to proactive cybersecurity.
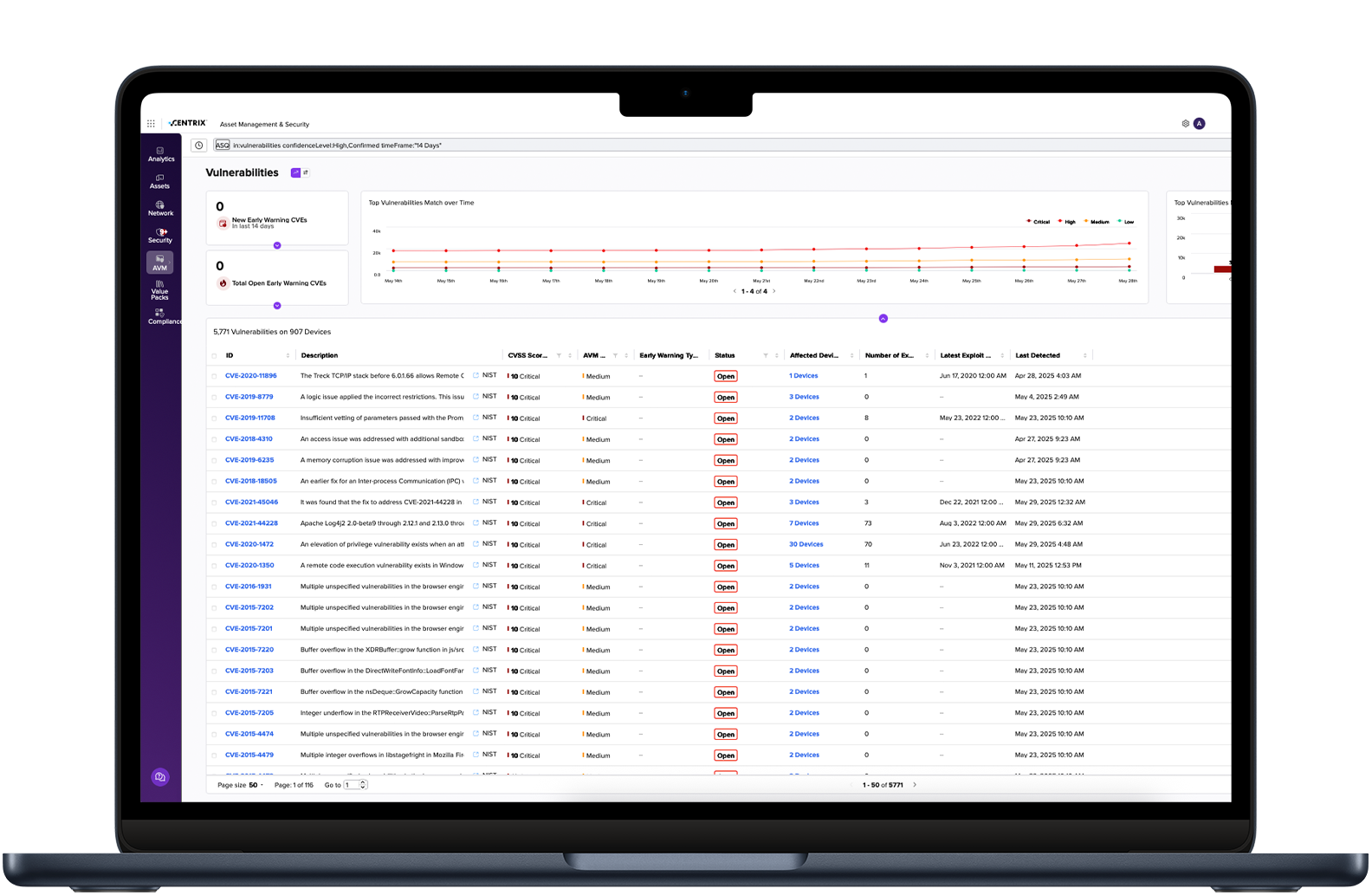
Compliance and Reporting
Transform the way you do security and flip the script on hackers by identifying and stopping attacks before they are even launched. Armis Centrix™ for Early Warning uses cutting-edge AI technology that leverages intelligence on what threat actors are exploiting in the wild or are about to weaponize. Shift your focus from reactive chasing to proactive cybersecurity.
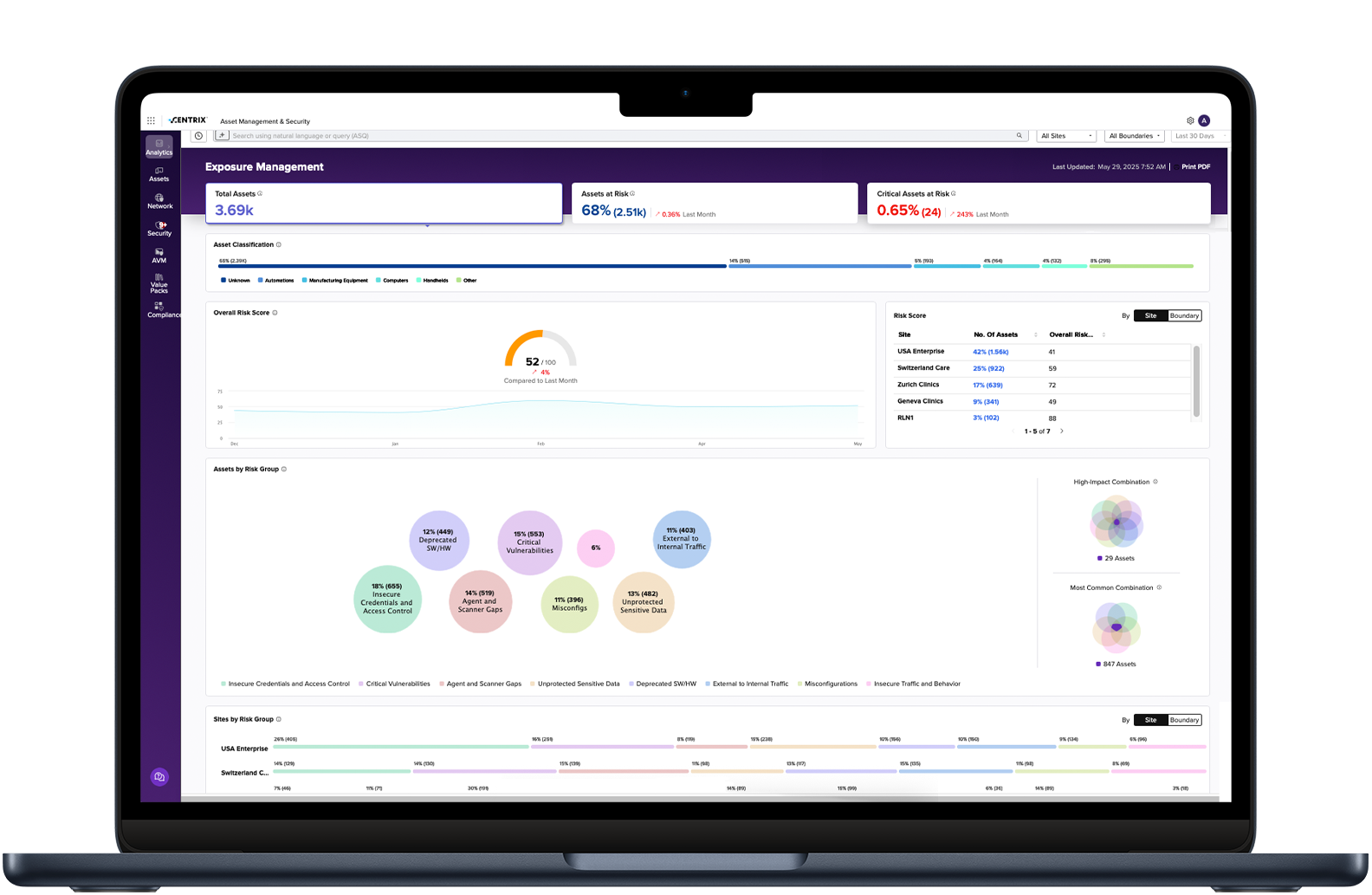
The Armis Exposure Management dashboard, provides a comprehensive view of your attack surface and exposures, both globally and with the ability to compare across sites or boundaries. This dashboard enables executives to:
- Understand the exposure landscape across their attack surface and track progress in reducing risk.
- Identify high-risk areas within the business and uncover the most common exposures.
- Save time and manual effort in collecting the data for reporting.