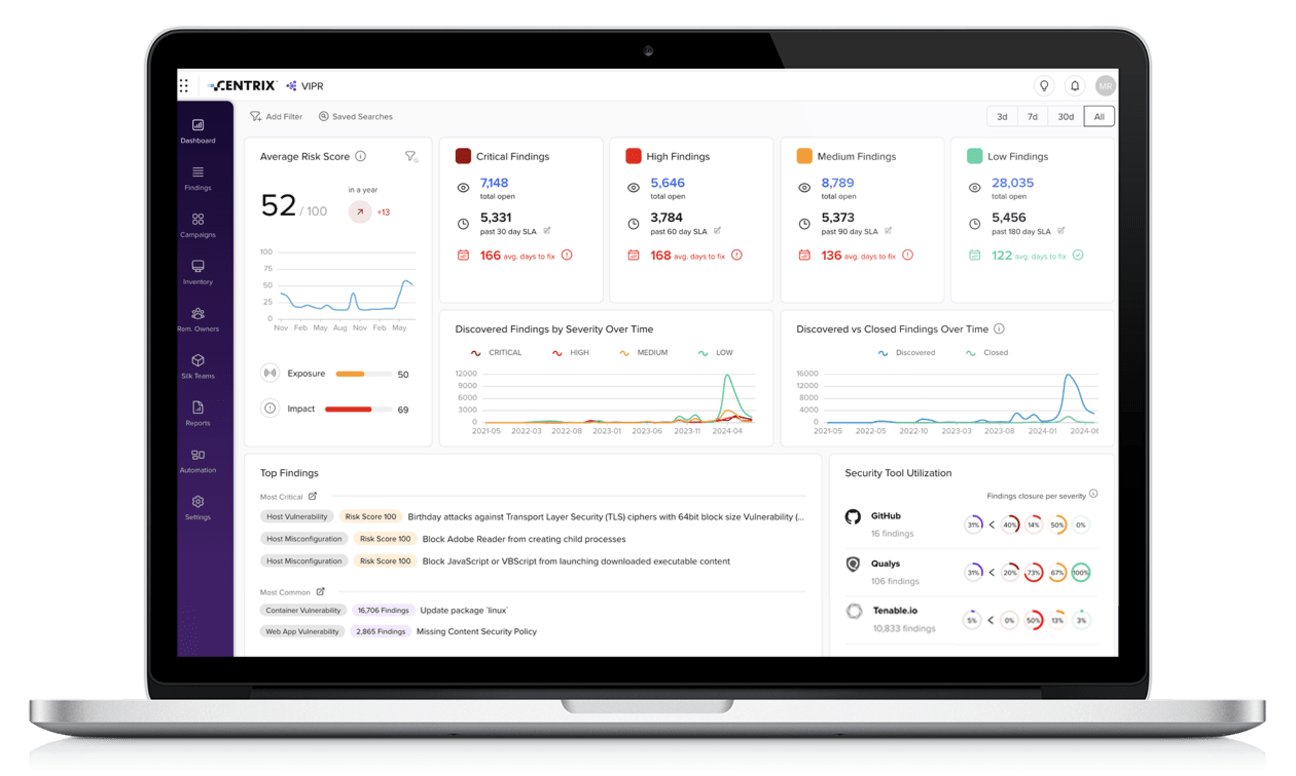
Intelligent risk tracking and resolution
Monitor and track the progress of risk mitigation efforts across your environment with AI-driven insights. With dedicated cyber exposure management dashboards and dashlets, you can quickly identify and address bottlenecks, ensuring that risk reduction is both efficient and effective.
Proactive threat prevention
Create automated workflows to help you take immediate, prioritized action on threats. Using our platform to do precisely this, organizations improve mean-time-to-resolution by up to 75%.
Streamlined compliance and oversight
Simplify compliance efforts with granular Role-Based Access Control (RBAC), pre-built integrations, and continuous monitoring. Armis Centrix™ ensures every action aligns with security frameworks and regulatory standards.
Moving to Proactive Security Stance Management
“Armis Centrix™ allows us to analyze vulnerabilities, raise service tickets to the appropriate individuals and teams, and gain a complete picture of vulnerabilities across our environment. Armis Centrix™ helps to reduce the operational load on our security team, while at the same time improving the efficiency of the vulnerability management process - from prioritization to remediation.”
Lehigh University (LU) is a private research university in Bethlehem, Pennsylvania. The university was established in 1865, and serves around 8,000 students.
The security team recognized that its vulnerability and exposure assessment process was not effective in prioritizing risk, which negatively impacted interaction with the teams responsible for implementing the fixes. In addition, the team was looking to reduce spend on multiple detection tools without compromising findings coverage.



Operationalizing a Risk-driven Continuous Threat Exposure Management (CTEM) Program
Organizations face an increasingly daunting challenge to identify and fix cyber exposure risk. Amplifying this challenge is the growing breadth and complexity of the attack surface incorporating IT, cloud, operational technologies, cyber-physical systems, and IoT assets, in tandem with a more sophisticated threat landscape – targeting not just traditional CVE vulnerabilities but also exposures including cloud misconfigurations, runtime, code, and application issues.
This white paper explores our findings from the Gartner® CTEM framework and discusses how we think Armis technologies can play a key role in enabling CTEM programs to ensure organizations maintain operational resilience while proactively minimizing their attack surface.